Hacking Applied: Hashcracking
Your (almost) complete guide
Hello, Hoodies!
We’re overdue for a paid stack, so here we go.
We’re continuing with the Hacking Applied series, and today we’re going over Hashcracking!
What is a hash?
It’s a string that’s the result of a hashing function.
What’s a hashing function? A 1 to 1 function where every unique input (is supposed to) produce a unique output of fixed length.
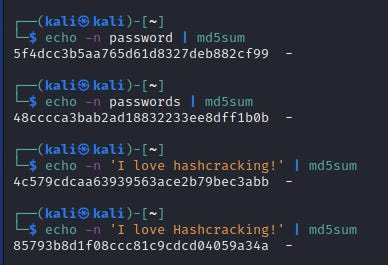
This is the md5 algorithm (which you’ll be familiar with if you studied your Net+ and Sec+). Even though it’s deprecated, it’s still incredibly common today.
Notice that each input has a different output, all of a fixed length. Changing one character changes the output dramatically.
Hashcracking is the process of going in reverse - starting with a hash and ending with an input.
But that’s impossible!!!
Yes it is. And that’s what makes it so much fun.
If you find this interesting and you want to start you Cyber Career, become a PAID HOODIE in the STACK. Everything you need to go from ZERO to HOODIE and into your first cyber job.
Now, let’s dive into hashcracking. Take it away, HoodieX!